Managed services platform(MSP)
Our managed services platform is built to monitor and manage customer networks 24/7 no matter how big customer infrastructure is. Our MSP infrastructure is made with redundancy at all levels in our data center. We use industry standard tools to monitor and manage customer infrastructure. Privacy is our main goal so we took all the precautions to isolate customer VPN tunnels from other customers.
Health and Welfare (Incident Management)
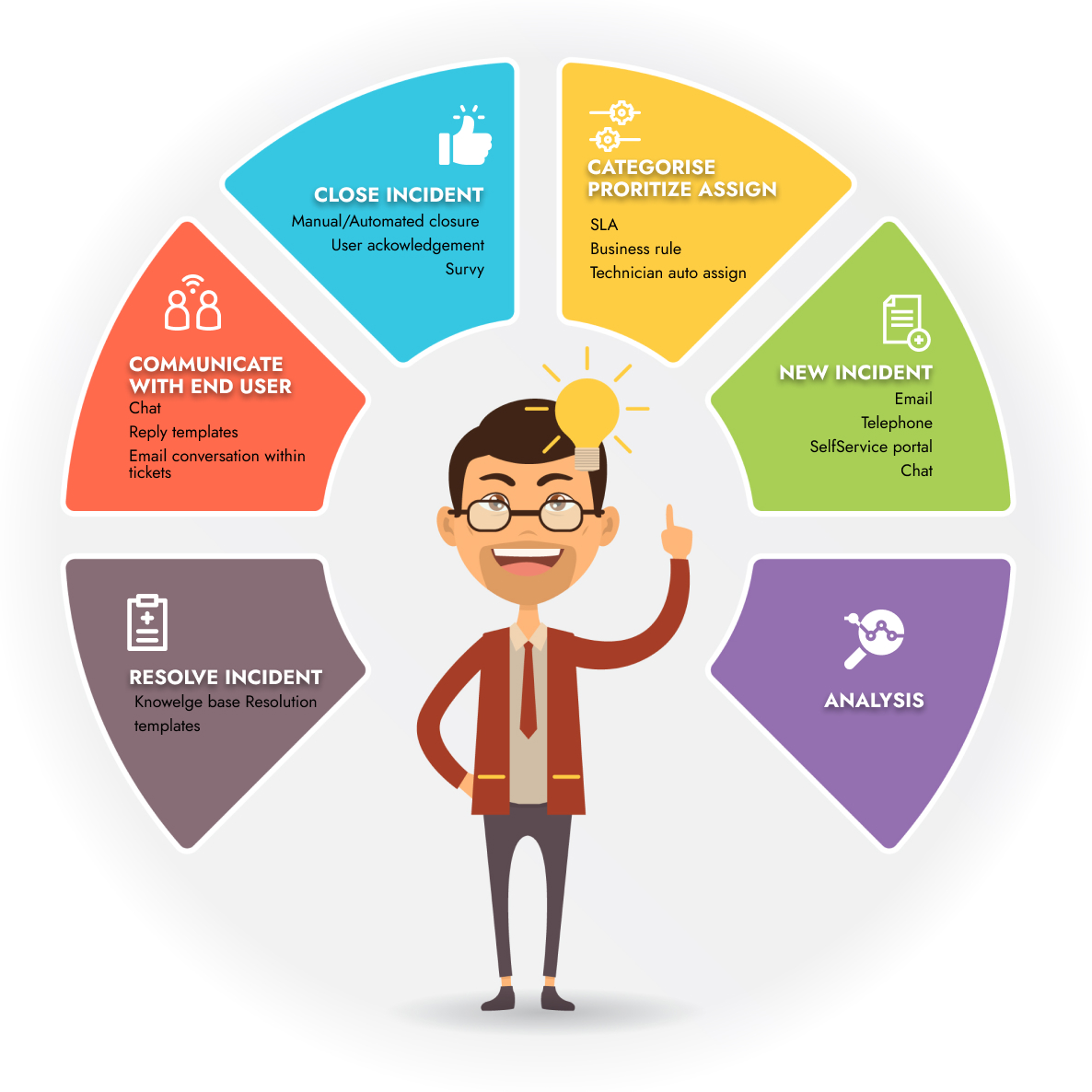 In this service, we monitor network devices using ICMP and SNMP. Our monitoring tools will monitor devices and report vis incident ticket whenever a device is down, or any resource reaches its set threshold. Our tools also have option to build custom SNMP queries to poll specific OID. Apart from network devices, we can also monitor any IP enabled device such as camera’s access control and etc.
In this service, we monitor network devices using ICMP and SNMP. Our monitoring tools will monitor devices and report vis incident ticket whenever a device is down, or any resource reaches its set threshold. Our tools also have option to build custom SNMP queries to poll specific OID. Apart from network devices, we can also monitor any IP enabled device such as camera’s access control and etc.
Our team at SOC-NOC will monitor customer network and its devices proactively and report them as per set process. We have team round the clock to provide this service 24/7. We will also provide our customer with portal to open incidents.
Incident Management restores normal service operation to contain the adverse impact on business operations, service quality, and availability. The monitoring and notification services provided by our platform work together with Incident resolution processes to form the Incident Management service component.
We will perform the following monitoring and notification services:
- Uses Incident remediation procedures to collect any additional data required to diagnose and match to known errors in our knowledge base
- Works to restore services within agreed service levels, initiating the Change Management process, as needed, for restoration
- Coordinates with customer to dispatch support personnel to customer premises to perform necessary onsite repairs as per the customer maintenance and support contract
- Remotely assists onsite personnel to facilitate service restoration, as needed
Change Management
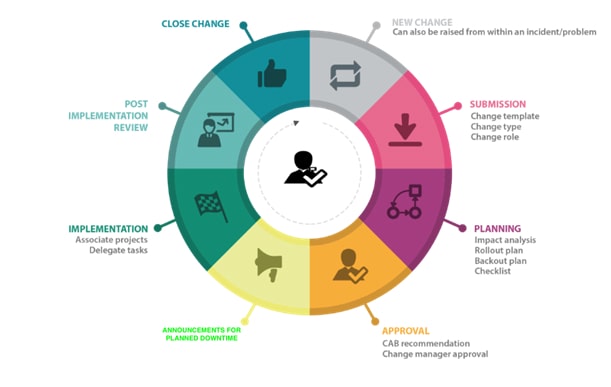 In this service we full fill customer change requests with a ticket. We will process every change through our set change management process such as CAB/TRB and prepare of MOP (Manual of Procedure). Once the change is fully approved by change management and customer, our engineers will implement them in approved window.
In this service we full fill customer change requests with a ticket. We will process every change through our set change management process such as CAB/TRB and prepare of MOP (Manual of Procedure). Once the change is fully approved by change management and customer, our engineers will implement them in approved window.
Our Change Management is based on the ITIL framework and provides governance over changes to the production environment. Formal procedures ensure the integrity and continuity of services.
Standardized procedures help manage the life cycle of requests for change. Our Change Management ensures that these changes are recorded, evaluated, prioritized, planned, tested, authorized, implemented, documented, and reviewed in a controlled manner
Log Management
Logs provides a way to ensure that critical events are logged and stored off the original server. An attacker's first effort after compromising a system is to cover the tracks left in the log. Events forwarded via syslog will be out of reach.
At Prowess Works, we manage and store logs from firewalls and other network devices. These logs can be used to investigate incidents and audit purpose. We use industry leading syslog tools such as Splunk, Nagios and etc.

DNS Security
We provide DNS security as a service. We have DNS server hosted in our datacenter and millions website categories based on website reputation. Our DNS server will block majority of spam, malware and spyware websites and most of adware on the websites. This will enable webpages to load faster. We can also perform web filtering using our DNS service if customer doesn’t have web filtering device in the network.
Customer will simply forward DNS requests to our cloud server and it will resolve based on the policy set. We frequently update our DNS database with latest list of malicious websites.
Vulnerability Assessment
While internet usage is increasing every day and reaching all over the world, it is also increasing the malware and other vulnerability-based attacks. It is very important for companies to scan all their devices especially their edge devices or internet facing devices for vulnerabilities and bugs.
At Prowess Works, we will
l perform weekly, monthly and quarterly vulnerability scans using industry leading tools on perimeter, internet facing and other devices. These report later will be used by change management to perform configurations, patches and upgrades to address vulnerabilities.
AMC
When any network device goes down, companies have to wait to get replace device through RMA process. This could take days or weeks depending on the contract. This could be huge loss to companies especially startups and mid-level companies. Their lack of backup devices in the inventory will cause network downtime.
At Prowess Works, we take complete care of your network infrastructure. If any network device goes down, such as firewall, router, switch and etc., we will provide backup device and get the faulty device repaired or replaced under warranty. We can deploy backup device in hours to bring up the network. We also have option to provide backup devices at sites.
Cloud Software’s
We provide various Cisco and other vendor products such as ISE, Firepower, WLC and etc over shared or dedicated cloud platform. This will enable customer to have enterprise level features at very low cost. This will also enable customer to have remote work force. In this service, we will custom build services to customers as per their needs. Our technical team will get in touch to understand current setup and plans to determine correct package.
Reporting
We will provide periodic reports on all our services. We will provide customers with online portal to view and pull historic data and reports


